It gives me a great pleasure to announce that after several months past the last release (see The HITB Magazine #6 now available!), the awesome crew (as always, special kudos to Zarul Shahrin) has managed to put up the 7th edition of Hack in the Box Magazine! Without much ado, I will just say that the issue presents some interesting bits about the current global crysis in the cyberspace (by Jonathan Kent), extending SQL Injection attacks through buffer overruns (Aditya K Sood, Rohit Bansal and Richard J Enbody), automation of fuzzing and process crash testing with the PCMCA tool (Jonathan Brossard) and a number of other interesting articles and book reviews.
It gives me a great pleasure to announce that after several months past the last release (see The HITB Magazine #6 now available!), the awesome crew (as always, special kudos to Zarul Shahrin) has managed to put up the 7th edition of Hack in the Box Magazine! Without much ado, I will just say that the issue presents some interesting bits about the current global crysis in the cyberspace (by Jonathan Kent), extending SQL Injection attacks through buffer overruns (Aditya K Sood, Rohit Bansal and Richard J Enbody), automation of fuzzing and process crash testing with the PCMCA tool (Jonathan Brossard) and a number of other interesting articles and book reviews.
In order for the magazine to function properly, we are in constant need of unique content. If you believe you have some interesting, IT Security-related material to present, and would like to contribute to the project, don’t hesitate to drop us a line (editorial@hackinthebox.org)! We will be more than happy to consult your idea, help with the correction, or provide with any other type of advice :-)
As for the Windows Security section, you can traditionally find an article authored by me, titled Windows Security Hardening Through Kernel Address Protection. The paper briefly describes the problem of revealing potentially sensitive information about the kernel virtual address space into user-mode code, lists the scenarios in which such information might prove useful during practical exploitation, and proposes potential solutions on both Windows and CPU levels.
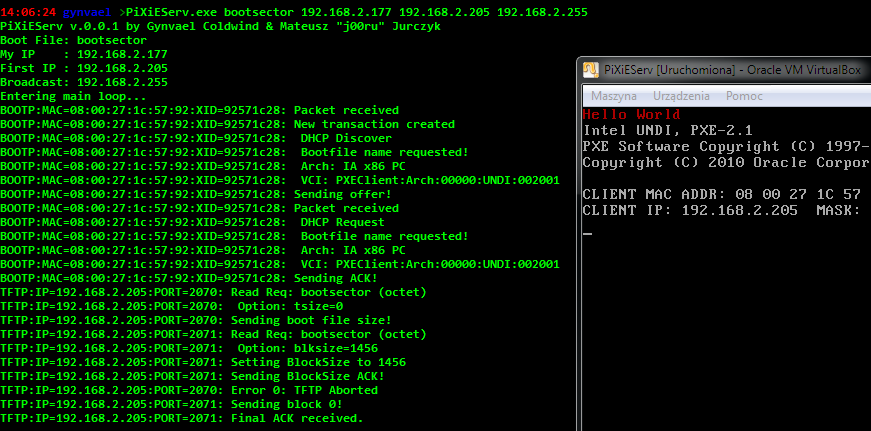
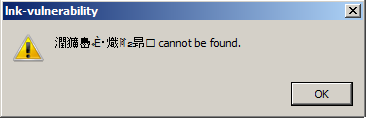
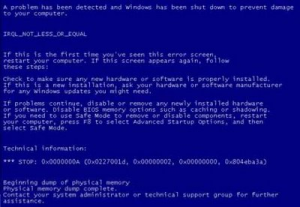 A rather short blog post today, as I am currently on my vacations. After publishing two, quite extensive write-ups regarding vulnerabilities in the Windows “CSRSS” component at Microsoft July Patch Tuesday:
A rather short blog post today, as I am currently on my vacations. After publishing two, quite extensive write-ups regarding vulnerabilities in the Windows “CSRSS” component at Microsoft July Patch Tuesday: As usual, I would like to inform you that the sixth issue of the Hack in the Box Magazine has just been published. Unlike previous editions, the paper is released several weeks after the HITB Amsterdam 2011 security conference – we spent the additional time working on providing you with even more interesting sections and articles. Despite the strictly technical articles (covering Web, Network, Linux, Windows and Application security areas), you can also find two unique interviews: one with the Facebook CSO Joe Sullivan, and the other one with Chris Evans and Adam Mein (members of the Google Security Team), discussing a variety of advantages, disadvantages, issues and benefits related to the famous Vulnerability Reward Program.
As usual, I would like to inform you that the sixth issue of the Hack in the Box Magazine has just been published. Unlike previous editions, the paper is released several weeks after the HITB Amsterdam 2011 security conference – we spent the additional time working on providing you with even more interesting sections and articles. Despite the strictly technical articles (covering Web, Network, Linux, Windows and Application security areas), you can also find two unique interviews: one with the Facebook CSO Joe Sullivan, and the other one with Chris Evans and Adam Mein (members of the Google Security Team), discussing a variety of advantages, disadvantages, issues and benefits related to the famous Vulnerability Reward Program.