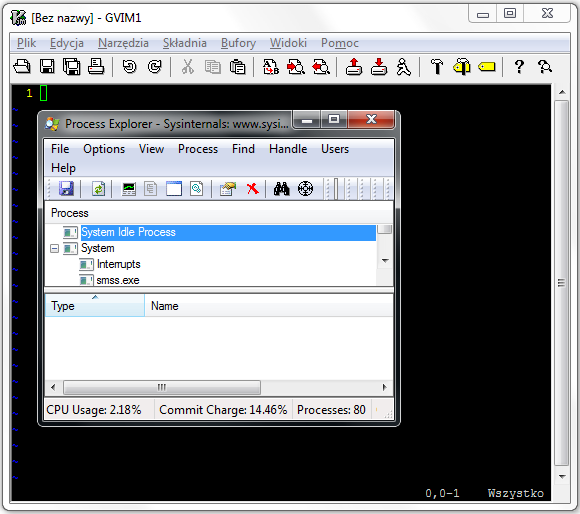
Having the first spare weekend in a really long time, I have decided it was high time to update some (all) of the tables related to Windows system calls and CSR API I once created and now try to maintain. This includes NT API syscalls for the 32-bit and 64-bit Intel platforms, win32k.sys syscalls for 32-bit and 64-bit Intel platforms, as well as CSR API information formatted in two different ways for convenience (a list and a table). Without further ado, all of the tables now contain up-to-date data covering all operating systems available to me at the time, including Windows 8, 8.1 and Server 2012. The links are as follows:
NT system calls
- Windows X86 System Call Table (NT/2000/XP/2003/Vista/2008/7/8)
- Windows X86-64 System Call Table (NT/2000/XP/2003/Vista/2008/7/2012/8)
Win32k.sys system calls
- Windows WIN32K.SYS System Call Table (NT/2000/XP/2003/Vista/2008/7/8)
- Windows x86-64 WIN32K.SYS System Call Table (NT/2000/XP/2003/Vista/2008/7/2012/8)
CSR API calls
- Windows CSRSS API List (NT/2000/XP/2003/Vista/2008/7/2012/8)
- Windows CSRSS API Table (NT/2000/XP/2003/Vista/2008/7/2012/8)
Pointers to all tables can also be found in the left pane under the “OS Structures” section. If you spot a bug in any of the tables or have any other comments, let me know. I hope you find them useful!
 Just yesterday I had the pleasure to speak at a highly hacking-oriented Russian conference,
Just yesterday I had the pleasure to speak at a highly hacking-oriented Russian conference, 
 This is a quick reminder that
This is a quick reminder that